Nov
21
2011
When you setup a corporate Exchange mail system users can access their mailbox on most mobile devices (iPhone, Android, Windows Phone…) through the ActiveSync protocol. For blackberry owners to access your mail system, you need to setup a BES infrastructure.
Read more »
Nov
04
2011
This script compares the updates approved between two WSUS target groups. It can ben useful when you want to get the differences between a test and a production group, you can read this Group Policy Central article to get more details on how to set up a WSUS test group using GPO (chapter Implement a WSUS Update Test Group of Computers).
Read more »
May
31
2011
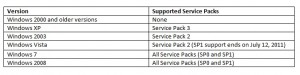
In this post we will describe how to make a WSUS clients inventory, we will search for the computers in your domain which are not able to receive MS security updates because they are not supported any more or because there is a misconfinguration on the WSUS client. Below is a tab listing supported OS and Service Packs versions:
Read more »
Apr
29
2011
We will show in this post how to create a SAN certificate for IIS 7 using an Enterprise PKI. This kind of certificate permits you to host multiple SSL sites on a single server. To achieve this with a powershell script we will use the PSRemoting and the IIS CmdLets.
We launch the script from the server where we administrate the PKI with ADCS RSAT. We will use PSRemoting for many things: Before sending the certificate request to the Certificate Authority in order to create the CSR on the IIS server. Once the certificate is issued we will retrieve it and install it to the IIS 7 server certificate store. Finally we will configure IIS 7 to use this certificate on the default web site.
Read more »
Mar
30
2011
In this post we will set up firewall rules using Group Policy Objects under Windows 2008 Server. When you install a windows role or feature the installer will configure firewall rules automatically upon installation. Some third party installers reconfigure the default Windows Firewall port settings and no further configuration is needed (e.g. Xenapp 5.0 for Windows 2008 to allow incoming connections, such as those from ICA traffic and the IMA service), some others don’t… For those applications we will configure the firewall rules and import those settings into an existing GPO with the netsh advfirewall command.
Read more »
Feb
08
2011
After an AD domain migration, some user accounts migrated in the target domain were not membres of the domain users group. In order to identify those accounts we used the following ActiveRoles Management Shell command:
Get-QADUser -NotMemberof 'ldap389\domain users' | export-csv domusers.csv |
Get-QADUser -NotMemberof 'ldap389\domain users' | export-csv domusers.csv
Read more »
Jan
06
2011
In order to edit GPO permissions with Powershell you can use the Set-GPPermissions CmdLet shipped with the RSAT (import-module grouppolicy). This Cmdlet does not have a replace permission option, nor does it let you set up a deny ACE on a GPO. In this post we will explain how to replace permissions on a GPO object thanks to the Security Descriptor Definition Language. This language is used to edit permissions in string format on all kind of objects (file system, registry, AD objects…). For a better understanding of the SDDL and a tool that translates a SDDL string you can read this post.
When do you need to replace permissions on a GPO? When an “OU administrator” account which is a member of the “OU administrators” group creates a GPO (and links it to an OU of his site), he is the owner of this object, members of the “domain admins” group can edit this GPO, but members of the“OU administrators” group cannot. So you might want to edit your GPO’s security settings by replacing the “OU administrator” account which created the GPO with the group that includes all the “OU administrators”. In our example, the domain has two sites, each one represented by an OU, we have two types of GPOs: Read more »
Nov
19
2010
Repadmin monitors the replication in your Active Directory Forest, you can read this AskDs post about this tool. The command line “repadmin /replsum” helps you retrieve the global forest replication status. The data retrieved for a given Domain Controller is:
- Largest Delta: longest time since he successfully replicated all the Naming Contexts with his replication partners.
- Number of failed replications that occured for all the Naming Contexts (aka Directory Partitions) with his replication partners.
The purpose of the powershell script is to analyse DC’s inbound replication thanks to the command line “repadmin /replsum /bydest”. If there are RODCs in your domain they do not show up if you use the /bysrc switch. You can read this post if you need to know more about running the repadmin /replsum command in a domain with RODCs.
If for a given DC the “largest delta” exceeds a given threshold (in minutes), or there are replication failures, we will read on the RootDSE object the msDS-ReplAllInboundNeighbors attribute. With that information we will retrieve which replication partners and “Naming Contexts” that are having trouble to replicate. You can retrieve the same type of information with the “replsum /showrepl %dc_name% /csv” command line, but the data stored in the msDS-ReplAllInboundNeighbors attribute is in XML format, which easy and convenient to manipulate with Powershell.
Read more »
Sep
17
2010
In this article we will describe how to search for a GPO matching several settings with Powershell. In this post and this one Lindsay Harris describes how to achieve this by exporting GPO reports in XML format and parsing the output. The principal advantage of her method is that you can input very precise search critera, but the disadvantage is that the script time processing can be very long because you need to export XML reports for every GPO in your domain. The method I will describe is more efficient in terms of script time processing but your search critera will be limited.
Read more »
Sep
06
2010
When you install Windows 2008 Certification Authority a new domain controller certificate template named Kerberos Authentication is available. It replaces the Domain Controller Authentication template. If you need more information about the new certificate templates shipped with a Windows 2008 CA you can read this article.
Here is a tab that outlines the specific attributes of the Domain Controller Authentication and Kerberos Authentication templates:
| |
Domain Controller Authentication |
Kerberos Authentication |
| Key Usage |
Client Authentication
Server Authentication
Smart Card Logon |
Client Authentication
Server Authentication
Smart Card Logon
KDC Authentication. |
| Subject Alternate Name |
DNS Name : Domain Controller FQDN. |
DNS Name : Domain FQDN.
DNS Name : Domain NetBios name. |
Read more »

