Jun
17
2013
We will show in this post how you can gather evidence of a potential remote attack on your Windows computer with some Powershell one-liners. This is done by analyzing the security log with the Get-EventLog cmdlet and by displaying active remote connections with the Netstat command.
Read more »
Mar
15
2013
In order to control what processes are running on your clients you can use the Software Restriction Policies or tools like Applocker or Bit9. You can also increase the security of you system on the allowed processes by enabling some mitigations like DEP, ASLR, SEHOP… We will describe in this post how to use EMET: A tool provided by Microsoft which allows you to configure these features. By protecting the processes running on your computer with these features you can even be protected against some 0-day exploits.
Read more »
Oct
07
2012
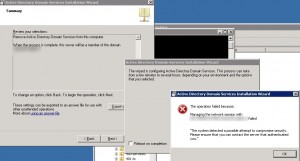
When demoting a domain controller the following error message appeared:
The operation failed because: Managing the network session with dc-srv2.ldap389.local failed.
“The system detected a possible attempt to compromise security. Please ensure that you can contact the server that authenticated you.”
Read more »
Sep
08
2011
This article describes how to digitally sign an Excel VBA project with a certificate issued by your ADCS PKI. You can use the same method to sign any Office VBA project but in this post we will focus on Excel. For an introduction on how to sign Office macros you can read these KB and MSDN articles.
Read more »
Aug
23
2011
In this post we talk about loopback processing of group policy and what interesting new feature is available when combining with Group Policy Preferences.
If you need a detailed explanation on how loopback processing of group policy works I suggest you read this 4sysops two part blog post (part 1, part 2).
Read more »
Jul
28
2011
In this post we will discuss some issues we had when using Microsoft Management Consoles to manage DNS (dnsmgmt.msc), Group Policy Objects (rsop.msc, gpmc.msc) and AD accounts (dsa.msc). No, we don’t use just powershell or command line tools to manage a Microsoft infrastructure: We click a lot 🙂
Read more »
Mar
30
2011
In this post we will set up firewall rules using Group Policy Objects under Windows 2008 Server. When you install a windows role or feature the installer will configure firewall rules automatically upon installation. Some third party installers reconfigure the default Windows Firewall port settings and no further configuration is needed (e.g. Xenapp 5.0 for Windows 2008 to allow incoming connections, such as those from ICA traffic and the IMA service), some others don’t… For those applications we will configure the firewall rules and import those settings into an existing GPO with the netsh advfirewall command.
Read more »
Jan
31
2011
In this post we will describe some issues we had when extending the schema for Active 2008 or 2008R2. The steps to prepare the schema for AD 2008 are described in this askDS post.
Read more »
Jan
06
2011
In order to edit GPO permissions with Powershell you can use the Set-GPPermissions CmdLet shipped with the RSAT (import-module grouppolicy). This Cmdlet does not have a replace permission option, nor does it let you set up a deny ACE on a GPO. In this post we will explain how to replace permissions on a GPO object thanks to the Security Descriptor Definition Language. This language is used to edit permissions in string format on all kind of objects (file system, registry, AD objects…). For a better understanding of the SDDL and a tool that translates a SDDL string you can read this post.
When do you need to replace permissions on a GPO? When an “OU administrator” account which is a member of the “OU administrators” group creates a GPO (and links it to an OU of his site), he is the owner of this object, members of the “domain admins” group can edit this GPO, but members of the“OU administrators” group cannot. So you might want to edit your GPO’s security settings by replacing the “OU administrator” account which created the GPO with the group that includes all the “OU administrators”. In our example, the domain has two sites, each one represented by an OU, we have two types of GPOs: Read more »
Sep
17
2010
In this article we will describe how to search for a GPO matching several settings with Powershell. In this post and this one Lindsay Harris describes how to achieve this by exporting GPO reports in XML format and parsing the output. The principal advantage of her method is that you can input very precise search critera, but the disadvantage is that the script time processing can be very long because you need to export XML reports for every GPO in your domain. The method I will describe is more efficient in terms of script time processing but your search critera will be limited.
Read more »

