Dcpromo: the system detected a possible attempt to compromise security
When demoting a domain controller the following error message appeared:
The operation failed because: Managing the network session with dc-srv2.ldap389.local failed.
“The system detected a possible attempt to compromise security. Please ensure that you can contact the server that authenticated you.”
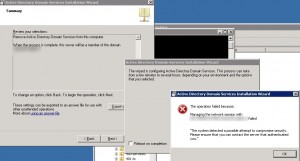
Having a look at the dcpromo.log did not tell us much:
10/04/2012 11:24:02 [INFO] Error – Managing the network session with dc-srv2.ldap389.local failed (1265)
10/04/2012 11:24:02 [ERROR] Failed to establish the session with dc-srv2.ldap389.local: 0x4f1
10/04/2012 11:24:02 [INFO] The attempted domain controller operation has completed
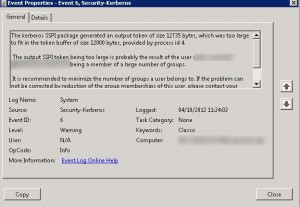
So we had a look at the eventlog, no errors regarding the dcpromo operation, but we noticed the following warning:
The event ID 6 from source Kerberos means the kerberos token size of the authenticated user is too large: The solution was to remove this administrator account from a few groups in order to decrease its kerberos token size, after that operation the error message disappeared and we were able to successfully demote the domain controller.
Under Windows 2008/7 the default maximum token size is 12000 bytes, under Windows 2012/8 it is 48000 bytes. This default value can be modified by GPO, however before modifying this value it might be interesting to find out which maximum token size best fit your environment. To achieve this you can use the tokensz.exe tool, but this can turn out to be a laborious task. Under Windows 2012/8 a new GPO setting allows you to generate warnings in the domain controllers eventlog when a large kerberos token is issued, you define the threshold yourself, by aggregating all those warnings you can define the right MaxTokenSize value for your environment, everything is explained in this AskDS post.
This post is also available in: French
2 Comments
Other Links to this Post
RSS feed for comments on this post. TrackBack URI


By MadSat, August 13, 2014 @ 5:05 pm
A rare problem to encounter, but I’ve had it happen in large enterprize environments. A good infomative post. Thank you.
By Rajh, August 5, 2016 @ 9:07 am
Thanks for this article. I’ve been trying to work out while this was happening in our environment for a group of admins, didn’t occur to me it was Kerberos token size as there were none of the other traditional symptoms.