Powershell: Enterprise CA, Create SAN certificates for IIS7 servers
We will show in this post how to create a SAN certificate for IIS 7 using an Enterprise PKI. This kind of certificate permits you to host multiple SSL sites on a single server. To achieve this with a powershell script we will use the PSRemoting and the IIS CmdLets.
We launch the script from the server where we administrate the PKI with ADCS RSAT. We will use PSRemoting for many things: Before sending the certificate request to the Certificate Authority in order to create the CSR on the IIS server. Once the certificate is issued we will retrieve it and install it to the IIS 7 server certificate store. Finally we will configure IIS 7 to use this certificate on the default web site.
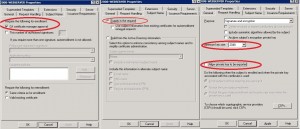
First we have a look at the certificate template named 2008-Webserver, which is a duplicate from the default WebServer template:
Once the certificate request is submitted to the CA, it must be approved by a CA Manager. Subject information (SAN) is supplied in the request (CSR). Minimum key size is 2048 bits and the key is not exportable. CSR will be created with certreq.exe which uses a RequestPolicy.inf file as an input option that defines the certificate request parameters.
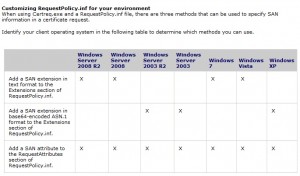
In that file we will add the Subject Alternate Name extension (i.e. the multiple URLs) to a particular section of the RequestPolicy.inf file:
You can find the above screenshot in this technet article, We will add the SAN to the Extensions section of the file. For security reasons you should never allow SAN certificates issuance by editing the RequestAttributes section on an Enterprise CA, do this only if you have a standalone CA.
Let’s have a look at the RequestPolicy.inf file ($iisinf):
[Version]
Signature=”$Windows NT$”[NewRequest]
Exportable = FALSE
KeyLength = 204
RequestType = CMC
[RequestAttributes]
CertificateTemplate= 2008-WEBSERVER[Extensions]
2.5.29.17 = “{text}”
_continue_ = “dns=webURL1.ldap389.info&”
_continue_ = “dns=webURL2.ldap389.fr&”
_continue_ = “dns=webURL3.ldap389.info&”
In order to build the CSR file on the remote IIS server ($webserver) with the certreq -new command, we will use the Invoke-Command CmdLet. If you want more information about PSRemoting I suggest you read Ravikanth Chaganti’s eBook.
Now you need to submit the CSR file ($iisreq) to the CA ($CAPath):
$array = @($CAPath,$iisreq) $Requestforsigning = invoke-command $webserver {param($argarray);certreq.exe -config $argarray[0] -submit $argarray[1]} -ArgumentList $array,$null $reqt = $Requestforsigning[0].replace('RequestId: ','') |
Before the certificate is issued the request ID ($reqt) has to be accepted by a CA manager (you 🙂 ), for that use the certutil -resubmit $reqt command.
After that we need to retrieve the certificate ($iiscrt = ‘iis.crt’) and install it to the IIS 7 server certificate store, we use the Invoke-Command CmdLet again in order to launch powershell commands on the remote web server:
$array = @($reqt,$iiscrt,$CAPath) invoke-command $webserver -scriptblock { param($argarray) certreq -config $argarray[2] -retrieve $argarray[0] $argarray[1] certreq -accept $argarray[1] } -ArgumentList $array,$null |
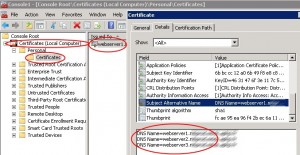
The SAN certificate is now installed in the local computer certificate store:
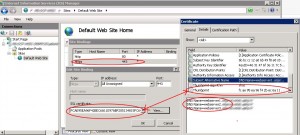
Finally we need to configure IIS, to achieve this we will use the WebAdministration CmdLets and follow the instructions given in this post. First we need to retrieve the certificate thumbprint using the certutil -view command:
$thumbprint = ((((certutil -view -restrict "RequestID=$reqt" -out CertificateHash csv)[1]).replace(' ','')).replace('"','')).ToUpper() |
Then launch the following script on the remote IIS 7 server:
import-module WebAdministration New-WebBinding -Name "Default Web Site" -IP "*" -Port 443 -Protocol https cd IIS:\SslBindings Get-Item cert:\LocalMachine\MY\$thumbprint | new-item 0.0.0.0!443 |
There you go, your IIS server is set up and ready to share multiple HTTPS URLs on the same server.
Download the full script here:
You just need to change the following variables:
- $CAPath: Certificate Authority path, %CA_Server_FQDN%\%CA_Name%
- $webURL1, $webURL2, $webURL3: URLs to put in the SAN certificate, you will need to adapt the script if the number of URLs is different.
- $CertTemplate: Name of your Webserver certificate template.
- $webserver: IIS 7 server name.
This post is also available in: French