Powershell: Edit GPO security settings
In order to edit GPO permissions with Powershell you can use the Set-GPPermissions CmdLet shipped with the RSAT (import-module grouppolicy). This Cmdlet does not have a replace permission option, nor does it let you set up a deny ACE on a GPO. In this post we will explain how to replace permissions on a GPO object thanks to the Security Descriptor Definition Language. This language is used to edit permissions in string format on all kind of objects (file system, registry, AD objects…). For a better understanding of the SDDL and a tool that translates a SDDL string you can read this post.
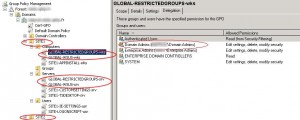
When do you need to replace permissions on a GPO? When an “OU administrator” account which is a member of the “OU administrators” group creates a GPO (and links it to an OU of his site), he is the owner of this object, members of the “domain admins” group can edit this GPO, but members of the“OU administrators” group cannot. So you might want to edit your GPO’s security settings by replacing the “OU administrator” account which created the GPO with the group that includes all the “OU administrators”. In our example, the domain has two sites, each one represented by an OU, we have two types of GPOs:
- GPOs named “GLOBAL-*” created by members of the “domain admins” group, they are linked to both SITE1 and SITE2 OU, those GPOs cannot be modified by the “OU administrator” group.
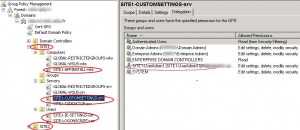
- GPOs named “SITEx-*” created by the SITE1 or SITE2 “OU administrators” group (SITE1-ADM and SITE2-ADM), by default the user account which created the GPO is the object owner (for example: Site1-UserAdmin1 for the SITE1 OU):
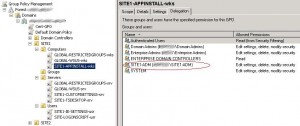
You need to replace the Site1-UserAdmin1 account with the SITE1-ADM group on the GPO ACL:
The Powershell script will search for the Group Policy Objects named “SITE1-*” and where the SITE1-ADM group does not have “full control” rights on the object (critera used: delete object). The resulting GPOs will be corrected by replacing the permissions. The Quest Active Roles Management Shell for AD will be used.
The Get-QADPermission CmdLet can read the permissions on the GPOs named “SITE1-*”, if the SITE1-ADM group does not have the delete object permission, then we search the account ($AdminAccount) which does, by using this command:
Get-QADPermission $gpo | foreach-object {if (( $_.AccountName -like $domain + '\*' ) -and ($_.Rights -like '*delete*')){$AdminAccount = $_.AccountName}} |
Once $AdminAccount is identified we get its SID (Site1-UserAdmin1 SID = $oldsid). We also export the GPO permissions in SDDL string format by using the Get-QADObjectSecurity CmdLet. In that string we replace the $oldsid value with the SITE1-ADM group SID ($newsid value). Finally we need to import the new SDDL string in order to edit the security settings on the GPO, we use the following commands to perform this task (read this BSonPoSH post for more details).
$sddlgpc2 = $sddlgpc.replace($oldsid,$newsid) $DE = [ADSI]"LDAP://$gpodn" $DE.psbase.ObjectSecurity.SetSecurityDescriptorSddlForm($sddlgpc2) $DE.psbase.commitchanges() |
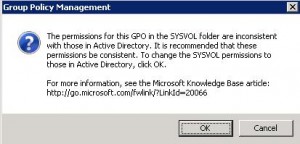
At this stage you have just edited the permissions on the Group Policy Container part of the GPO. If you try to edit the GPO with GPMC you will get the following error message:
This is because you also need to replace the permissions on the Group Policy Template part of the GPO which is a folder named GPO GUID located on the SYSVOL share. To achieve this we will use the Set-acl CmdLet which includes the SetSecurityDescriptorSddlForm function which is convenient to export and import SDDL strings, like described in this article.
You can download the full script here:
You just need to edit the following variables:
- $domain: Domain NetBios name.
- $domainFQDN: Domain FQDN.
- $siteadmgrp: OU admins group.
- $gpoprefix: Prefix of the GPOs which are managed by the “OU admins” group.
Launch the REPLACE_SDDL_GPO.ps1 script, you will be prompted before the replace operation proceeds:
This post is also available in: French