Conficker causes lsass process overconsumption
If lsass process consumes too much CPU time on your domain controller the cause might be clients infected by Conficker. The link to the KB article discusses how to prevent its propagation and how to remove the worm. The purpose of this post is to identify infected clients which cause this lsass.exe overconsumption easily.
This topic was already discussed in a post of AskDS, I’ll add a few comments and scripts which will help you to eradicate the virus on your workstations.
The most efficient methodology to reach our goal was to use a GPO that audits the failed logon attempts on the DC. Create a GPO and apply security filtering on the DCs where the problem occurs. Apply the following parameters:
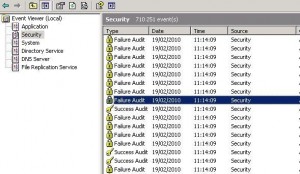
Refresh Group Policy and you should see these events in the security eventlog:
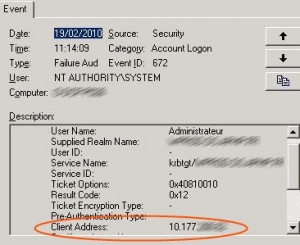
Keep the audit running for a few minutes then disable the GPO in order to prevent overloading of the security eventlog. Let’s now have a clooser look on Event ID 672:
The field “Client Adress” gives us the IP adress of the infected client. Because there are thousands of events like this we need to perform a script that parses the description of each event to get the client infected and then count the occurences of each client, in order to know on which workstations we need to remove the virus in priority.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 | 'Enter Name of your DC strComputer = "XXXXXX" Const ForReading = 1, ForWriting = 2, ForAppending = 8 Set fso = CreateObject("Scripting.FileSystemObject") sCurPath = fso.GetAbsolutePathName(".") Set FLog = FSO.CreateTextFile(sCurPath&"\ip.txt") Set objWMIService = GetObject("winmgmts:" _ & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2") 'Get time one hour ago dtmCurrentDate = DateAdd("h", -1, now) 'Format time dtmTargetDate = Year(dtmCurrentDate) dtmMonth = Month(dtmCurrentDate) If Len(dtmMonth) = 1 Then dtmMonth = "0" & dtmMonth End If dtmTargetDate = dtmTargetDate & dtmMonth dtmDay = Day(dtmCurrentDate) If Len(dtmDay) = 1 Then dtmDay = "0" & dtmDay End If dtmTargetDate = dtmTargetDate & dtmDay dtmHour = Hour(dtmCurrentDate) If Len(dtmHour) = 1 Then dtmHour = "0" & dtmHour End If dtmTargetDate = dtmTargetDate & dtmHour dtmTargetDate = dtmTargetDate & "0000.000000" dtmTargetDate = dtmTargetDate & chr(43) & Cstr(120) 'search all EventID 672 occuring one hour ago Set colLoggedEvents = objWMIService.ExecQuery _ ("SELECT * FROM Win32_NTLogEvent WHERE Logfile = 'Security' AND EventCode = '672' AND TimeWritten >='"&dtmTargetDate&"'") For Each objEvent in colLoggedEvents 'parse the Message IP is between Client Adress and Certificate Issuer Name message = objEvent.Message message1 = split(message,"Client Address:") messagef = split(message1(1),"Certificate Issuer Name:") FLog.Writeline (messagef(0)) Next msgbox "View all IPs in ip.txt, now lets count occurences" FLog.close Set df1 = fso.OpenTextFile(sCurPath&"\ip.txt",ForReading,True) Set FLog2 = fso.CreateTextFile(sCurPath&"\result.csv") Dim IPCOUNT(80000,2) 'Initialize counting table for j=0 to 80000 IPCOUNT(j,0) = "0" IPCOUNT(j,1) = 0 Next 'read lines of ip.txt and save result in table, if a new IP is discovered a new column is filled in with IP otherwise counter is increased by one Do while Not df1.AtEndOfStream IPTST = df1.readline() marque = "non" if IPTST <> "" then i=0 Do While IPCOUNT(i,0) <> "0" if IPCOUNT(i,0) = IPTST then IPCOUNT(i,1) = IPCOUNT(i,1) + 1 marque = "oui" End if i = i + 1 Loop if marque = "non" then IPCOUNT(i,0) = IPTST IPCOUNT(i,1) = 1 End if End if Loop df1.close 'write table result in text file for k=0 to 80000 FLog2.writeline(IPCOUNT(k,0)&";"&IPCOUNT(k,1)) Next msgbox "Done, Check result.csv" |
Download the vbs sample script:
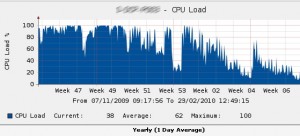
Now you have the most infected clients just proceed to the worm’s removal. Note that you will have to perform this kind of audit a few times before getting rid of the worm for good, simply because powered off computers are obviously not detected, another reason is that Conficker works on scheduled tasks and the task my be inactive during the audit. On a site which was very badly infected it took a few weeks to eradicate the virus, but the results are promising, just have a look at the CPU consumption of the DC:
If you cannot remove the worm on some clients because you can not reach them for any reason you can solve this CPU overconsumption by banning the IP adresses, this method is a bit extreme so use it sparingly. Just launch at the command prompt of your DC:
cmd /c route -p add %CLIENT_IP_ADRESS% MASK 255.255.255.255 %UNUSED_IP_ADRESS%
%UNUSED_IP_ADRESS% is an adress in the same subnet as your DC and does not respond to ping, therefore is not used. The “-p” switch means the route is permanent and will not be deleted when your DC reboots. Finally you need to perform this command on every DC the client can use as logon server.
This post is also available in: French
3 Comments
Other Links to this Post
RSS feed for comments on this post. TrackBack URI


By gorkem, June 10, 2010 @ 10:08 am
Script doesnt work.
line: 11
char : 1
error : 0x80041002
code : 80041002
Source : (null)
By gorkem, June 10, 2010 @ 10:38 am
Fixed it
Line 11 and 12 must be like this
Set objWMIService = GetObject(“winmgmts:” _
& “{impersonationLevel=impersonate}!\\” & strComputer & “\root\cimv2”)
By ldap389, June 10, 2010 @ 5:27 pm
Hi Gorkem,
Thanks for pointing this, for some reason my WordPress editor sometimes deletes the “\” character on the scripts I post, sorry about that.
Sometimes it adds some wired “;amp” characters as well, I try to correct this as much as possible but sometimes I don’t pay enough attention 🙁