Powershell: Forensic One-liners
We will show in this post how you can gather evidence of a potential remote attack on your Windows computer with some Powershell one-liners. This is done by analyzing the security log with the Get-EventLog cmdlet and by displaying active remote connections with the Netstat command.
You can find a cool one-liner that retrieves the events of the Account logon category in this Windows Logon Forensics whitepaper (chapter 6.4. Querying Events). The one-liner fetchs the following events which occurred during the past five days:
- A Kerberos authentication ticket (TGT) was requested.
- The computer attempted to validate the credentials for an account.
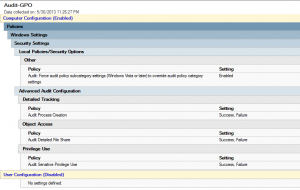
We were inspired by the one-liner presented in this document, downloaded at the SANS reading room, to make a Powershell one-liner the purpose of which is to gather proof of a potential attack on your Windows computer. First in order to have the relevant information in your security log you need to configure the advanced security audit policy settings. We will enable auditing for the following categories: Process Tracking\Process Creation, Object Access\Detailed File Share and Privilege Use\Sensitive Privilege Use. This can be done via GPO:
We enable the following parameter: Force audit policy subcategory settings to override audit policy category settings. Our computers are running Windows 7/2008R2. Beware of the consequences, legacy policies will be ignored.
Beware that you should not enable the Object Access\Detailed File Share setting on all types of servers: For example on a DC, because the SYSVOL share is often accessed by all your domain clients this setting will generate an important volume of logs to store/analyze.
The one-liner will search for the following events:
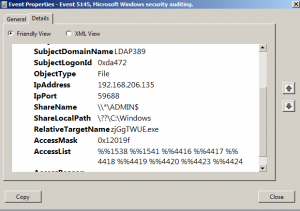
- Event ID 5145: Category Object Access\Detailed File Share, gives us information on the accessed shares. If one of the following administrative shares is accessed IPC$,ADMIN$,C$ and the access requested is a write access, %%4417 = WriteData(or Add File), then the event is returned.
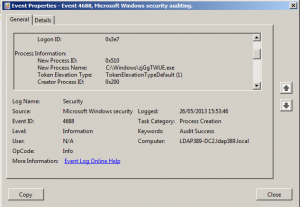
- Event ID 4688: Category Process Tracking\Process Creation, monitors every process creation. If the process TokenElevationType is TokenElevationTypeDefault (%%1936) or TokenElevationTypeFull (%%1937) the event is gathered.
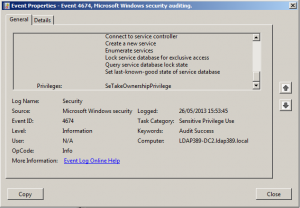
- Event ID 4674: Category Privilege Use\Sensitive Privilege Use, If the privilege requested is SeTcbPrivilege (Act as part of the operating system), SeTakeOwnershipPrivilege (Take ownership of files or other objects) or SeDebugPrivilege (Debug programs) the event is collected:
The following onliner searches for the three types of events described above which show up over the past 5 days:
get-eventlog -log security | where-object {$_.TimeGenerated -gt (get-date).adddays(-5) -AND $_.EntryType -eq 'SuccessAudit' –AND (($_.EventID -eq "5145" -AND $_.Message -match "\\\\\*\\ADMIN\$|\\\\\*\\C\$|\\\\\*\\IPC\$" -AND $_.Message -match "\%\%4417") -OR ($_.EventID -eq "4674" -AND $_.Message -match "SeTakeOwnershipPrivilege|SeDebugPrivilege|SeTcbPrivilege") -OR ($_.EventID -eq "4688" -AND $_.Message -match "\%\%1936|\%\%1937"))} | sort-object -property TimeGenerated |
In order to search patterns having special characters with a regular expression you need to use the “\” as an escape character.
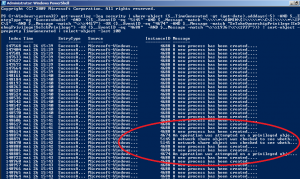
If the 3 events occur successively this might be an evidence of a remote attack on the machine:
The security logs show us that the remote attacker IP address is 192.168.206.135. We will use the netstat command in order to retrieve the active connections and check if the attacker is still connected:
The following one-liner displays the netstat output and gives us the name of the process used now by the attacker in a more readable format than the netstat -anb command:
netstat -ano | Select-String -Pattern '\s+(TCP|UDP)' | foreach-object{$item = $_.line.split(' ',[System.StringSplitOptions]::RemoveEmptyEntries);if(($item[2] -notmatch '127.0.0.1:|\[::1\]:') -and ($item[2] -ne '*:*') -and ($item[2] -ne '0.0.0.0:0') -and ($item[2] -ne '[::]:0')){($item[0]+"`t"+$item[1]+"`t"+$item[2]+"`t"+$item[3]+"`t"+(get-process -id $item[4]).Name) | ft}} |
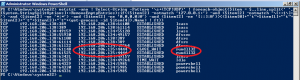
Here is the connection used by the attacker:
For a more advanced script on the use of netstat with Powershell check this script.
This post is also available in: French
3 Comments
Other Links to this Post
RSS feed for comments on this post. TrackBack URI

By Alain, August 26, 2016 @ 3:43 pm
Hi Leo,
In English, these would be “one-liners” and not “onliners” 🙂
By ldap389, January 28, 2017 @ 12:32 am
Yep, can’t believe I left this typo all those years… Thanks!
By Software Company in UAE|Software Company in Dubai|HR and Payroll Software|HR Management System|Accounting Software, April 14, 2017 @ 6:15 pm
You ought to take part in a contest for one of the best blogs on the
internet. I will recommend this site!